7 Outreach Tactics Cybersecurity Buyers Hate (+ The Alternative)
Jul 11, 2022
When I launched Audience 1st Podcast, I knew it would help me and you understand cybersecurity buyer motivations, needs, and challenges so that we can more efficiently help out those battling threats do their jobs just a little bit better.
Little did I know that it would open the floodgates to regular emails and LinkedIn messages coming to me from disgruntled security practitioners.
The amount of poor marketing and sales messages they send me is overwhelming.
-
How can I provide security professionals a safe space to flag ineffective emails, social media posts, website landing pages, event messages, or even digital ads?
-
More importantly, how can marketers and sellers engage with cybersecurity practitioners more meaningfully and authentically?
There are clear examples of what not to do.
But, what are the alternatives? How should we engage with them?
So, I created a destination for cybersecurity professionals who are targeted by vendors to submit the worst marketing and sales messages they’ve seen.
It’s called WTF Did I Just Read?.
Shoutout to Joseph Carson for explicitly asking for something like this AND for the inspiration.
Why is this important to the industry?
It’s not enough for buyers to bitch about what isn’t working, right?
That isn’t fair to you or me. We need to understand the alternative. We need to fix the problem.
How will this help you?
Upon submission, I've asked each security professional who flagged “bad behavior”, as they put it, to provide me a clear explanation of what not to do (the shitlist, if you will) and the alternative approach + simple tips to engaging with them.
-
You’ll learn effective methods to outreach high-consideration cybersecurity buyers.
-
You’ll be able to more authentically build real relationships with cybersecurity buyers that will boost your long-term career.
-
You’ll improve your (and your company’s) reputation as a marketer or a salesperson.
When can you expect the shitlist + alternatives?
Every month, I'm carefully curating each marketing and sales message submitted and providing the alternatives recommended by real cybersecurity practitioners.
I'll then post them on in the Audience 1st Vault when they come into my queue.
Here's a sneak-peek inside the security practioners' email inbox:
The Unsolicited Gift Card

The Alternative:
-
Do not send gift cards sent out in an unsolicited manner
-
If you are going to provide a meaningful gift, do not send a 3rd party website to get the gift.
-
Remove buzzwords like "Zero Trust"
-
Honestly ask for feedback, not business
The Competitor Outreach

The Alternative:
"Hi [Rep Name],
Maybe you would like to review our website and see what services we offer to clients ourselves before offering this to us. We are always open to getting ideas from our competitors.
Cheers,
[Head of Corporate Information Security]"
You Must Not Care
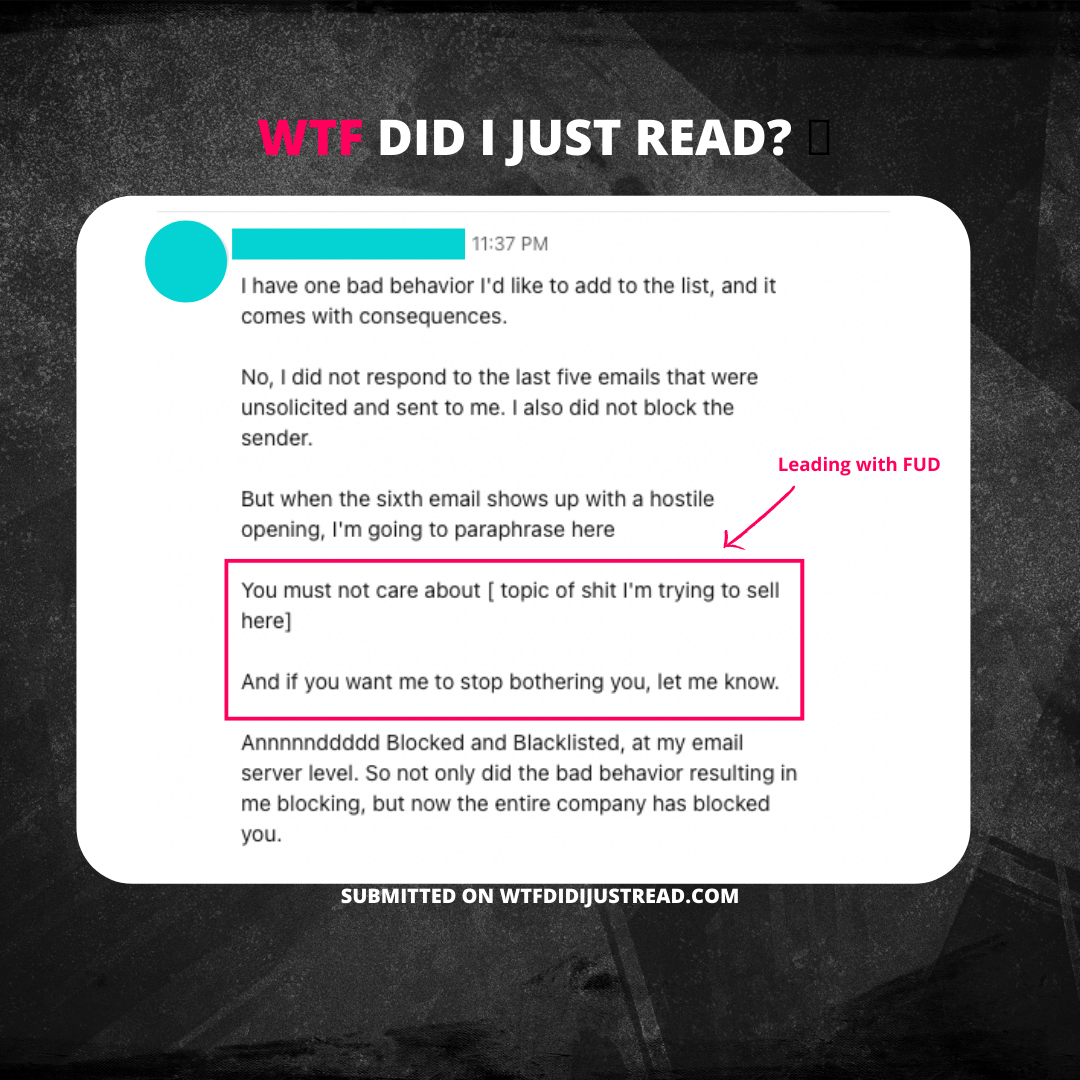
The Alternative:
-
Understand that cybersecurity practitioners get 1000s of emails a day.
-
NEVER lead with FUD (Fear, Uncertainty, and Doubt)
-
Get to know the interests of the person you are trying to reach
Premature LinkedIn-ulation

The Alternative:
-
Wait for a cybersecurity executive to settle into their new role.
-
Ask them how things are going.
-
Learn their business first.
-
Never pitch them services before they even start their position at their new company.
Won’t Take “No” for an Answer

The Alternative:
You Are the Chosen One (For $1500)

The Alternative:
"YOU are the chosen one, now pay me money so I can talk with the deity of your choice from the comfort of my own private jet…."
-
Do not persist in reaching out for a transaction if the security professional does not reply or says "no".
-
If you are going to give an award to someone or recognize them, do not ask them to pay for it.
Can We Be Friends? (And Oh Make $ For a Referral)

The Alternative:
"The ones that actually make it through the ones that are like, ‘Hey, I've got the bottle of Islay. Can we just have a conversation? We're doing this. Can we run it by you?’
If you're running it by cause you want an opinion, I'll give you all the time in the world, it doesn't matter who it is. I mean, I have marketing people like, ‘Hey, I just want to run things by you. Cause I don't want to trip over my feet.’
It's that honesty and integrity. I give leeway because everybody's got to sell, everybody's got to buy things, but it's how that transaction is conducted to me that is important.”
Cheers,
[CISO]
